VSFTPD 3.0.3 Exploit: The Untold Story You Need To Know
So, listen up, folks. We’re diving headfirst into the world of cybersecurity today, and it’s not gonna be pretty. If you’ve been keeping an ear to the ground, you’ve probably heard whispers about the infamous VSFTPD 3.0.3 exploit. It’s like that one drama-filled episode of your favorite TV show—chaotic, intriguing, and packed with twists. But instead of entertainment, this is serious business. Let’s break it down, shall we?
This ain’t just another tech jargon you can skim through. The VSFTPD 3.0.3 exploit has been making waves, leaving admins scrambling to patch up their systems before it’s too late. Think of it as a digital burglar slipping through the cracks in your house’s security system. Scary, right? So, buckle up because we’re about to uncover the nitty-gritty details that’ll keep your servers safe.
And hey, don’t worry if you’re not a cybersecurity guru. This article’s got your back. We’ll walk you through everything from the basics to the advanced stuff, ensuring you leave here armed with the knowledge to protect your digital fortress. Let’s get this show on the road!
- Isa Ramirez Only Your Ultimate Guide To Her Life Career And Achievements
- Reed Johnson Baseball Academy The Ultimate Training Ground For Future Stars
What’s the Deal with VSFTPD Anyway?
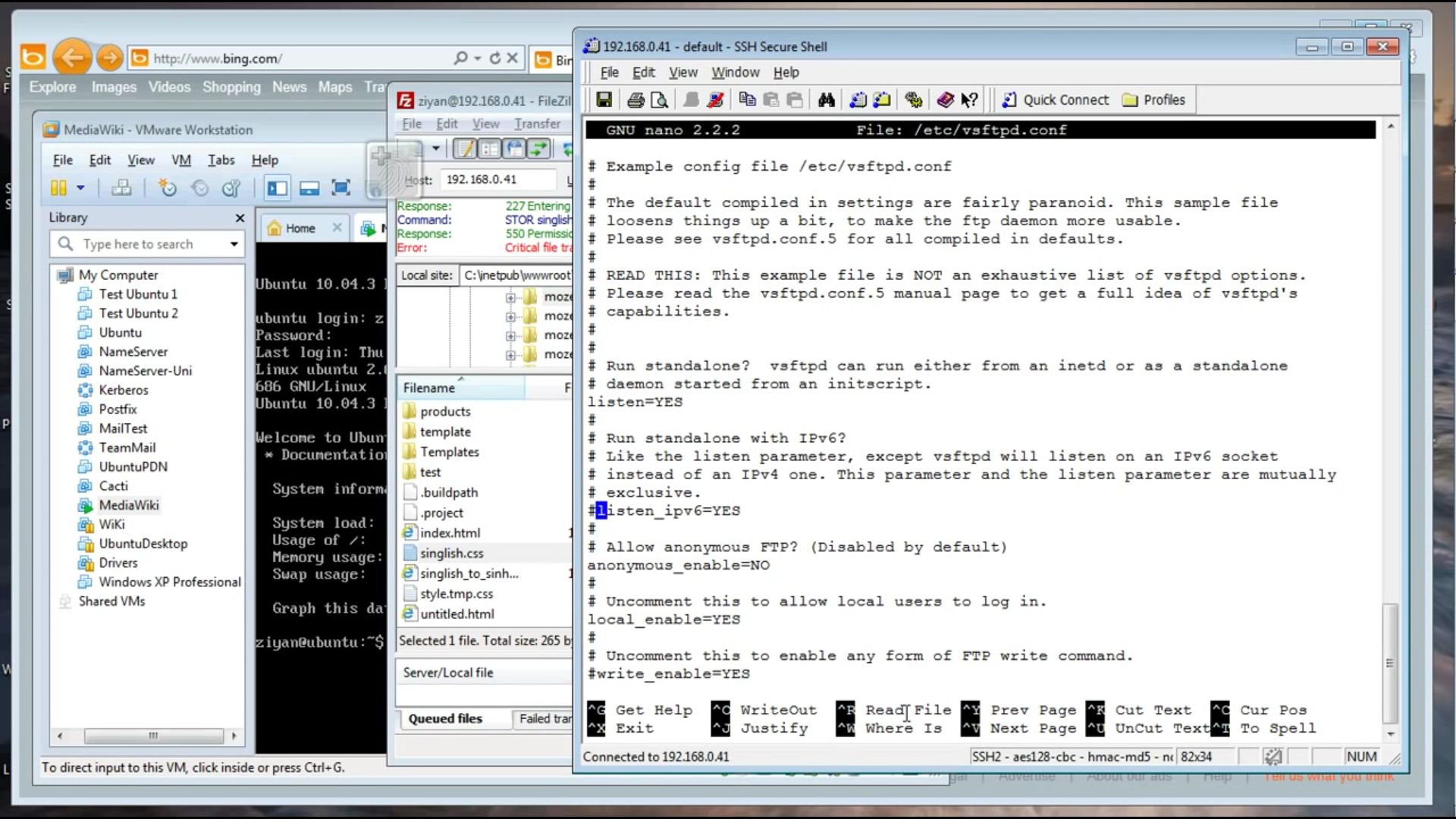
Let’s start with the basics, shall we? VSFTPD stands for Very Secure FTP Daemon. Yeah, I know, the name sounds like it’s trying to reassure us, but sometimes even the toughest-looking guards can have weak spots. VSFTPD is a widely used FTP server for Unix-like systems, and it’s been around for a hot minute. It’s known for being lightweight and secure—well, until version 3.0.3 came along and threw a wrench in the works.
Why Should You Care?
Here’s the deal: if you’re running a server with VSFTPD 3.0.3, you’re essentially leaving the front door wide open for hackers. This exploit allows attackers to gain unauthorized access to your system, and trust me, that’s not a situation you want to find yourself in. From stealing sensitive data to taking control of your entire network, the consequences can be catastrophic.
The Birth of the VSFTPD 3.0.3 Exploit
Every villain has an origin story, and so does our exploit. The VSFTPD 3.0.3 exploit was first discovered back in 2011. Now, you might think, “Wait, 2011? That’s ancient history!” But here’s the kicker: even today, there are systems out there still vulnerable to this exploit. It’s like leaving a time bomb ticking in your basement, hoping no one finds it.
- Christian Modeling Company Your Gateway To Faithbased Fashion
- What Does A Giraffe Symbolize Unveiling The Majestic Meaning Behind This Iconic Creature
How Does the Exploit Work?
Let’s get technical for a sec. The exploit takes advantage of a buffer overflow vulnerability in the VSFTPD software. In simpler terms, it’s like when you try to fit too much stuff into a box, and it bursts open. Attackers can craft malicious inputs that overflow the buffer, allowing them to execute arbitrary code on the server. It’s a hacker’s dream come true.
Who’s at Risk?
So, who exactly should be worried about this? If you’re running a server with VSFTPD 3.0.3, you’re on the list. But here’s the thing: even if you’re not directly using VSFTPD, there might be systems within your network that are. It’s like playing a game of Russian roulette—you never know when the bullet’s gonna hit.
Real-World Impacts
Let’s talk numbers. Studies show that thousands of servers worldwide are still vulnerable to this exploit. Imagine the chaos that could ensue if a hacker decided to target a major corporation. Data breaches, financial losses, and reputational damage are just the tip of the iceberg. And let’s not forget the legal ramifications that come with failing to secure your systems properly.
How to Protect Yourself
Now that we’ve painted a rather grim picture, let’s focus on the solutions. The first step is obvious: update your VSFTPD software. Seriously, folks, it’s 2023. There’s no excuse for running outdated software. But updating isn’t the only thing you should do. Here’s a quick list of additional measures you can take:
- Implement firewalls to block unauthorized access.
- Use strong, unique passwords for all your accounts.
- Enable two-factor authentication wherever possible.
- Regularly monitor your systems for suspicious activity.
Best Practices for Cybersecurity
While we’re on the topic of protection, let’s touch on some best practices that’ll keep your systems safe from not just the VSFTPD 3.0.3 exploit but any other threats lurking in the digital shadows.
First off, education is key. Make sure everyone in your organization understands the importance of cybersecurity. Conduct regular training sessions and keep them updated on the latest threats. Knowledge is power, after all.
Next, invest in robust security tools. There are plenty of options out there, from antivirus software to intrusion detection systems. Find the ones that work best for your needs and stick with them.
Understanding the Threat Landscape
The world of cybersecurity is constantly evolving, and so are the threats. What worked yesterday might not work tomorrow. That’s why staying informed is crucial. Keep an eye on industry news, subscribe to cybersecurity blogs, and join online communities where experts share their insights.
Common Misconceptions
There are a few myths floating around about the VSFTPD 3.0.3 exploit that need to be debunked. One of the biggest is that it only affects small businesses. Wrong. Big corporations are just as vulnerable, if not more so, due to the sheer volume of data they handle. Another myth is that once you patch the vulnerability, you’re good to go. Sorry to burst your bubble, but cybersecurity requires constant vigilance.
The Role of Ethical Hackers
Here’s where things get interesting. Ethical hackers, also known as white-hat hackers, play a vital role in identifying and mitigating vulnerabilities like the VSFTPD 3.0.3 exploit. They use their skills for good, helping organizations strengthen their defenses against malicious actors. It’s like having a superhero on your side, except instead of capes, they wear hoodies.
How Ethical Hackers Operate
Ethical hackers use a variety of techniques to test systems for vulnerabilities. Penetration testing, vulnerability assessments, and security audits are just a few of the tools in their arsenal. They work closely with organizations to identify weaknesses and provide actionable recommendations for improvement.
VSFTPD 3.0.3 Exploit: A Case Study
Let’s take a look at a real-world example of how this exploit played out. Back in 2012, a major online retailer fell victim to the VSFTPD 3.0.3 exploit. Hackers gained access to their servers, stealing sensitive customer data, including credit card information. The fallout was massive, costing the company millions in damages and tarnishing their reputation. It’s a cautionary tale that highlights the importance of staying vigilant.
Lessons Learned
From this case study, we can draw several important lessons. First, never underestimate the power of a seemingly small vulnerability. Second, always have a solid incident response plan in place. And third, prioritize cybersecurity as a core component of your business strategy.
Wrapping It Up
Alright, folks, that’s a wrap on our deep dive into the VSFTPD 3.0.3 exploit. Hopefully, you’ve gained a better understanding of what it is, how it works, and most importantly, how to protect yourself from it. Remember, cybersecurity is a marathon, not a sprint. It requires constant effort and dedication.
So, what’s next? Take action! Update your systems, implement the best practices we’ve discussed, and stay informed about the latest threats. And don’t forget to share this article with your friends and colleagues. Knowledge is power, and the more people who are aware of these issues, the safer we all are.
Until next time, stay safe out there!
Table of Contents
Article Recommendations
- Entourage Of Seven Glasses The Ultimate Guide To Elevate Your Drinking Experience
- Kaitlan Collins Gold Medallion Necklace The Ultimate Guide To This Iconic Piece

Detail Author:
- Name : Ms. Summer Wuckert
- Username : flueilwitz
- Email : chesley56@runolfsdottir.com
- Birthdate : 1974-03-15
- Address : 294 Tillman Greens Suite 954 West Edytheburgh, DC 31972-5869
- Phone : +1-781-563-9122
- Company : Pfeffer, McCullough and Bosco
- Job : Religious Worker
- Bio : Omnis totam vel odio ducimus neque. Et enim doloribus qui explicabo distinctio natus omnis perferendis. Nobis beatae quod itaque dolor qui et.
Socials
tiktok:
- url : https://tiktok.com/@johnsg
- username : johnsg
- bio : Et quidem ut porro et et illo.
- followers : 1547
- following : 1605
twitter:
- url : https://twitter.com/garfieldjohns
- username : garfieldjohns
- bio : Reprehenderit sunt recusandae consequatur. Repudiandae nostrum nobis dignissimos provident. Molestiae cupiditate corporis est.
- followers : 1974
- following : 1314